Virtual Private Network (VPN) can be described as a communication platform among computers in an organization. It may consist of connection companies, organizations or institutions or consist of departments in an organization. This networking method is done on public networking system, mostly the internet. It is done by securing systems referred to as network protocols. Providers will consider security, geographical coverage and speed as their main determinants of the infrastructure used. The provider will offer well secured service level agreement to their clients.
Operation of Virtual Private Networks (VPN):
A Virtual Private Network has two parts which are inner and the outer side. The inner side is designed in such a way that it provides administrative authentication permission and physical security to the person surfing via this network. The outer side is the public network which comprises of international connection to private and organization’s computers via a public network. The external side will pose the greatest threat to the security of a system. This is because many people have access to the links. All links are co-joined by the host or server from all parts of the world. When the user requires information, they will connect to the international host servers via personal browsers. This is done by an authenticated connection via a network. To protect intrusion and attack by malicious software as well as leakage of personal information to the international servers, the user is advised to install a firewall inn their work stations such as personal computers.
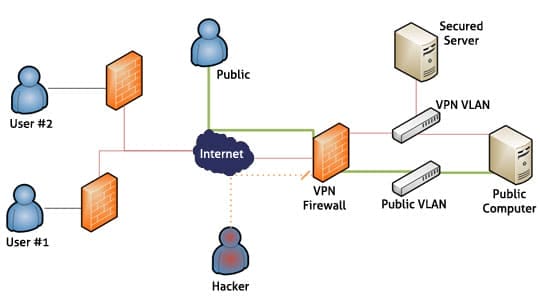
Major role of VPN providers:
The key consideration in virtual networking is security. This refers to the ability of a network to withstand external intrusion from unauthorized parties. The security is addressed by the use of encrypted protocols. The customer is assigned the specific key to their network. This key is to be used to authorize access to the Virtual Private Network. A firewall wall is a program designed to prevent unwanted programs and personalities from accessing a work station.
Configuration:
The network is laid in such a way that only the user has the ability to access the authentication. This is done by use of IP address which identifies the user to the server. The internet service provider (ISP) will require the specified protocol to connect the workstation to the server. The Virtual Private Network protocols includes the following:
- SSL which is used for tunneling the whole network stack which includes in the Open Virtual Private Network (VPN). This can also be regarded as a secured web proxy from the internet service provider.
- Point-to-point tunneling protocol (PPTP) was jointly developed by major companies in this field of technology, including Microsoft.
- Layer two tunneling protocol is also a major protocol in large scale connections. It was jointly developed by Microsoft and Cisco.
Security:
Security is a major concern because access by external parties will lead to information leaked to external media. The intruders include network hackers, external programs or unauthorized personnel in the departmental level in an organization.
The network providers offer Secure Virtual Private Networks (SVPNs). This method will prevent snooping. Sender authentication will serve to identify spoofs. Use of message integrity will prevent message alteration by external parties such as hackers. This methodology of securing networks will enable secure communication over unsecured networks.
There are four main types of security offered they include:
- Authentication (access control) –this ensures that the person using the network from a specific work station ID the legitimate owner. The method used here is a login password which is only known to the user. It will therefore enable the person to fist enter the correct password before the connection is made. Others use a fingerprint or a specified card key. To ensure a stronger authentication, the user is advised to combine more than one authentication method
- Presentation (encryption / privacy) – Encryption operation is founded on two principles which include a key and an algorithm. A mathematical combination of characters to give a specified string will be used. It is referred to as a cryptographic algorithm. The strength of an algorithmic encryption is based on the length of the string as well as the combination. The popular encryption keys include Advanced Encryption Standard. (AES), Elliptic curve cryptosystems (ECC).
- Transportation (data integrity) – it prevents any modification of the packets from the sender. It does this by ensuring that messages sent and received are from the right and recognized sites and have not been modified.
- Non repudiation (correct message reception) – it focuses on ensuring the integrity of E-Mails. This is done by ensuring that the email sent and received are from the right source and have not been manipulated during transfer.
For more reference visit the wiki page of Virtual Private Network.






