The wave of advanced technologies brings unprecedented opportunities for businesses and society. The emergence of the Internet of Things (IoT) represents a pioneering transformation in the field of information technology (IT) and digitization. These developments can improve & elevate a business environment to generate higher profit margins. IoT has the potential to bring a major transformation in business models, change competitive forces of several industries, and reduce time-to-market for a variety of products or services. While IoT promises several real-time operational benefits, susceptibilities can easily be exploited unless robust security measures are implemented across connected devices and infrastructures.
Some of the risk associated with both enterprise IoT and consumer IoT devices includes:
- Data storage management.
- Data security & privacy issues.
- Personal and public physical safety risks.
Curbing IoT data generation and leaks

The proliferation of IoT devices is consistently producing vast volumes of data. An autonomous vehicle, for instance, is anticipated to generate 2,000,000 gigabits of data each year. A smart building could end up generating over 200 gigabits of data per day. In light of the growing volumes of data and the risk associated with it, governments in several counties are establishing laws and regulations aimed to protect citizens’ personal information from unauthorized access to IoT systems and data. For instance, compliance with regulations such as the U.S. Consumer Product Safety Improvement Act of 2008, the Sarbanes-Oxley Act (SOX), the U.S. IoT Cybersecurity Improvement Act of 2017, the Federal Information Security Management Act (FISMA), and the U.S. Developing Innovation and Growing the Internet of Things (DIGIT) Act, among others, ensure that IoT systems are protected from unauthorized access and data theft.
Moreover, the Cloud Security Alliance (CSA) is anticipated to bring new guidelines for best security practices for everything connected to the internet from drones to smart cities. Furthermore, the European Union’s (EU) General Data Protection Regulation (GDPR) aims to create a rigid environment for several businesses and may impose civil & criminal prosecution, regulatory fines if companies fail to protect data on citizens belonging to EU countries. These acts and other government initiatives enable a secure environment for users and necessities IoT device manufacturers to promote the use of best practices for providing security assurance.
Besides, there are significant efforts taken by IoT OEMs to prevent cyber-attacks. IoT devices manufacturer are potentially making security as one of the top priorities during all phases of device development. For instance, several OEMs are anticipated to provide lifecycle device update to eliminate the challenges of a threat to the devices. Moreover, a company offering improved security solutions to protect IoT devices would likely become a market differentiator. Thus, IoT device manufacturers are not only offering a smart device but also providing continuous security upgrades to generate more revenue than that of a rival company.
Recommended for you: VPN vs RDS vs VDI: What to Choose for a Secure Remote Access?
IoT hacks that happened in the past few years

From head-mounted displays to fitness trackers and even connected home appliances, smart devices & IoT systems are collecting an increasing amount of user data and gaining privileged access to connected devices. A growing number of malicious threats have significantly jeopardized the privacy and security of a connected system. For instance, in 2017, hackers successfully attempted to acquire data from a U.S.-based casino by using an internet-connected fish tank. It is estimated that more than 10 gigabytes of data were leaked before the intrusion was detected and blocked.
Hackers are continually looking for new ways to access people’s data. For instance, in 2016, a series of distributed denial-of-service attacks were launched on the systems of cloud-based internet performance management company Dyn. The attacks disrupted services from platforms such as The Guardian, Twitter, Reddit, Netflix, and CNN, among others, resulting in huge revenue losses. A large number of IoT-enabled devices were exploited by cybercriminals using a malware named Mirai. The malware continually searched the cyberspace for susceptible IoT devices and then used known passwords and usernames to log in, infecting them. With the number of devices connecting to the internet is rapidly increasing in verticals such as healthcare, automotive, manufacturing, and consumer appliance, the risk posed by them is augmenting.
The growing importance of network security

Consumers have become increasingly dependent on smart devices, thereby sharing personal information with them. Moreover, wireless devices and smart technologies are frequently being utilized in the workplace, posing a growing risk to a company’s sensitive data. As these IoT devices are connected to a wider corporate network, they become a vulnerable point of the network, posing a significant security threat to an enterprise. Thus, networks connected to these devices have grown to be more valuable than ever before. With the rapid growth of cyber-attacks on the underlying network infrastructure connected to these devices, several enterprises, as well as individuals, are taking a pro-active interest in network security and device scanning tools.
Security plays an essential role within all the phases of an IoT product’s/service’s lifecycle. These phases include conceptualization & design, deployment, and maintenance. Beside these phases, protecting the underlying networking infrastructure from threats such as unauthorized access, misuse, malfunction, alteration, and improper disclosure of personal information pays a vital role in the development of an IoT device
Network security practices play an important role in securing IoT devices. They secure and protect the network connecting IoT devices to back-end systems on the internet. The key competency of a typical network security plan includes endpoint security features such as antimalware and antivirus as well as other features such as IDS/IPS and firewalls. Other practices undertaken under network security ensure that systems are patched and are up to date, ports are secured, unauthorized IP addresses are blocked, and the port forwarding process is disabled and ports are never opened when not needed.
Securing IoT devices network to sophisticated cyber-attacks provides substantial benefits to both consumer and enterprise including:
- Utilization of global real-time threat intelligence coupled with the ability to use several kinds of databases and technologies.
- The risk of protecting the network is handled by the CSPs expert, minimizing the consumer concerns of protecting the device.
- Managing the threat in real-time before it attacks the device.
- Covering the mass market of IoT security.
- Application of centralized solution ensures the protection of devices and endpoints independently.
Besides, organizations are increasingly focusing on the use of strong user authentication and access control methods such as the multifactor authentication and secure encryption method WPA2. Enterprises are encrypting the network, regardless of whether or not they have an IoT environment.
Additionally, the intrusion detection system and intrusion prevention (IDS and IPS) systems are increasingly being adopted to monitor network vulnerabilities and network gateways. Furthermore, enterprises are splitting the network into a series of sub-networks coupled with the managed gateways to restrict the flow of information. Such methods ensure that only authorized users gain access to system and data, thereby supporting good network security practices and mitigating malicious access to the network.
The proliferation of IoT devices and the consecutive rise in privacy and security concerns
The IT companies have increased their investments and efforts to enhance and boost the adoption of advanced technologies such as Artificial Intelligence (AI) and IoT, products, services, and ecosystems around IoT. These developments are anticipated to offer a wide range of benefits to entice both business and consumer. Thus, as the number of connected IoT devices steadily increases, the demand for network security solutions and services are anticipated to grow at an impressive pace in the next few years. Moreover, the need for security features such as authentication and data integrity measures such as secure remote administration and configuration are anticipated to boost the demand of internet of the things security market.
According to the study published by Grand View Research on IoT Security Market, the IoT network security type market size is expected to reach USD 2,824.1 million by 2025.
Global IoT network security market size, by region 2015–2025, (USD Million)
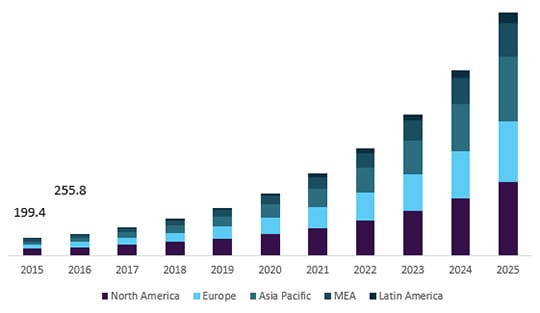
Image Source: Grand View Research
The emergence of smart industry, smart city, smart home, and smart things are expected to boost IoT adoption. Looking at applications in the healthcare sector, smart bands, for instance, are witnessing increased popularity on the consumer front for monitoring health on an everyday basis at the comfort of one’s home. More than 15 billion devices, with varying features and applications spanning several industries, are expected to connect to the internet by the end of 2020. The number is projected to cross 30 billion by 2025. This massive increase in the number of connected devices. However, this is also likely to create security concerns by opening up a new vector of opportunities for cyber-criminals to gain access to financial and other private data. Providing a layered security approach to cyber defense while minimizing the data collected by such devices, IoT network security is increasingly becoming the need of the hour.
You may also like: Risks and Dangers of Smart Gadgets: How to Stay Protected?
Article Summary

Dynamic changes in technology have increased consumer expectations from new products and services. Companies are catering to these expectations with products enabled by advanced technologies such as IoT. IoT-enabled devices making waves in the consumer market include smartwatches, thermostat, and fitness bands. IoT products are also transforming the way organizations operate. These developments have increased the complexity of the IoT ecosystem, thereby increasing the vulnerabilities of IoT-enabled devices. Thus, to control the dynamic IoT ecosystem, there is a growing need to secure the devices from the processes such as conception, deployment, and maintenance, to the network edge. Thus, our research suggests that hardware and software technologies embedded in network security solutions are expected to be the first line of defense in securing the platform of IoT devices.
This article is written by Anoop Rao. Anoop is an experienced professional with a demonstrated history of working in the market research industry. He is currently working at Grand View Research in the Information and Communication Technology (ICT) team. Anoop has over 2+ years of experience, supported by specialty in qualitative and quantitative analysis. He has worked across several areas, including end-to-end reports and clients consulting projects. Anoop is skilled in Go-To-Market strategy, industry analysis, in-depth company profiling, value chain & supply chain analysis, and market sizing, among others. He is also versed with topics such as security, automation, and compliance. Anoop holds a Post Graduate Diploma in Management (PGDM) from MIT-School of Business, Pune.
 This article is written by Anoop Rao. Anoop is an experienced professional with a demonstrated history of working in the market research industry. He is currently working at Grand View Research in the Information and Communication Technology (ICT) team. Anoop has over 2+ years of experience, supported by specialty in qualitative and quantitative analysis. He has worked across several areas, including end-to-end reports and clients consulting projects. Anoop is skilled in Go-To-Market strategy, industry analysis, in-depth company profiling, value chain & supply chain analysis, and market sizing, among others. He is also versed with topics such as security, automation, and compliance. Anoop holds a Post Graduate Diploma in Management (PGDM) from MIT-School of Business, Pune.
This article is written by Anoop Rao. Anoop is an experienced professional with a demonstrated history of working in the market research industry. He is currently working at Grand View Research in the Information and Communication Technology (ICT) team. Anoop has over 2+ years of experience, supported by specialty in qualitative and quantitative analysis. He has worked across several areas, including end-to-end reports and clients consulting projects. Anoop is skilled in Go-To-Market strategy, industry analysis, in-depth company profiling, value chain & supply chain analysis, and market sizing, among others. He is also versed with topics such as security, automation, and compliance. Anoop holds a Post Graduate Diploma in Management (PGDM) from MIT-School of Business, Pune.




