Article Note: This article “17 Best Cybersecurity Tips to Stay Protected Online in 2022” was first published on 28th May 2020. We have last updated this article on 11th March 2022 with fresh information.
You’ve likely heard this statement time and time again – the need for cybersecurity continues to increase year after year. No matter how often we hear that statement, the threat against cybersecurity still remains prevalent, especially in our emails and our local small businesses.
The truth is, almost half of cyber-attacks get directed at small businesses. Even if you use a username generator (such as offered by NordPass) to use strong passwords and change them regularly, is that enough to protect people on the internet?
Our world made a significant shift in 2020 due to the Covid-19 pandemic. The global shutdown forced many businesses to offer remote working to keep their doors open. As you remove workers from the business hub and have them conduct their duties outside the office, you soon understand the demand for cybersecurity. It’s more essential than ever to ensure everyone has adequate protection while online and connecting to a network.
Whether you’re working remotely or surfing the web in your free time, taking steps to stay protected will keep you and your personal data safe. We have a list of many tips to boost your cybersecurity and remain protected.
The growing need for cybersecurity

Streaming services powered by affordable and reliable options like Cox cable bundles have changed the entire game for the entertainment industry. However, the emergence of new technologies has created different challenges for individuals and businesses alike.
The past several years have seen an unprecedented surge in cybersecurity attacks around the globe. These attacks have disrupted entire supply chains and cost millions of dollars in loss to multi-national corporations such as banks and tech companies.
Recommended for you: How is Machine Learning Used in Cybersecurity?
Increasing data on reliance

The importance of analyzing and interpreting data cannot be overstated in this digital age. Companies rely on qualitative and quantitative variables for multiple reasons. Using data insights offers tremendous benefits. It is safe to say that data mastery ensures growth and success for years to come. Name a business that doesn’t use data. Restaurants, online advertisers, retail outlets – all use data to improve their customer services.
This ever-increasing reliance on data creates an urgency for companies and businesses to take data protection measures. Computer criminals do not discriminate between individuals and companies. They are always on the lookout for their next target. Organizations need to realize the importance of adopting cybersecurity measures before it’s too late. The bigger the target, the more valuable it becomes for hackers to exploit.
Adoption of remote work

No doubt, the pandemic has forced companies to make difficult decisions. Workplace chatter and in-house meetings seem like a distant memory. The fact that a mere bug brought the world to its knees is difficult to digest. The emergence of the virus prompted companies to shift critical in-house operations to remote locations.
Work from home becomes the new work culture. Adjusting to the new routine may have been difficult for many. This unprecedented transition also brought with it new kinds of security threats. Because so many people adopted work from home, computer criminals came up with new methods to disrupt remote servers.
The work-from-home culture is here to stay. There’s no denying that but companies need to be proactive on the security front. Employees working from home may be vulnerable to cyberattacks. Organizations must invest in information security training to bring them up to date with the latest digital security trends.
Tools for digital communication

People have come a long way since the days of MSN Messenger and Myspace. Today, the world has Facebook (now Meta), WhatsApp, and Instagram to name a few. You could download dozens of social networking apps and not get fed up. Why? Because, while the core functionality of these apps is the same, they come with different features.
For every user, there exist multiple social profiles. You have your Gmail ID, your Facebook profile, your WhatsApp contact info, etc. The advent of so many communication tools has enabled hackers to steal identities and extort money from their targets. Unless you do not beef up your digital security, you will remain vulnerable to cyberattacks and information security threats.
Supply chain automation

Businesses around the world are starting to adopt automation tools. Why? Because automation has the power to change things for the better. Automation practices reduce arduous labor hours. They reduce costs associated with manufacturing and assembling. Automation tools allow businesses to achieve productivity and efficiency. However, implementing automation tools without focusing on their security is a risk in itself. Hundreds of industries around the world have adopted automation tools but how many of them know the cons associated with it.
Cybersecurity threats are continuing to emerge despite efforts by experts to tackle information security challenges. The key is to be vigilant with technology. Applications and programs are great as long as you remain cautious and watchful with their use.
Types of cybersecurity threats

Cybercrime has witnessed tremendous growth in the past decade. This is particularly the case with the increasing popularity of the Internet and its usage across the world’s remote places. According to statistics revealed by cybersecurity ventures, the amount of money lost to cybercriminals is expected to hit $6 trillion marks in 2021, which is a 50% increase in the amount lost in 2015. There are also threats and fears among cybersecurity firms that cybercriminals have increased their use of sophisticated technologies to bypass security checks.
If you listen to the experts, according to the 2020 cybersecurity statistics published by Sven Taylor of Restore Privacy, “Last year we talked about cyberattacks that aimed not to steal data, but to destroy it. While the cost of recovering from a cyberattack may be enough to drive a business under, that isn’t the primary goal of most attacks. However, this year we may see a large increase in the number of attacks specifically aiming to damage or destroy businesses through the destruction of their data.”
The increase of daring attacks from cybercriminals on small and medium businesses as well as personal attacks has made cybersecurity a crucial issue for the next decade. With all these in mind, we look at the top 10 cybersecurity threats today.
You may like: What You Should Know About AWS Cloud Security Issues.
1. Internet scams

Internet scams have long been a major cybersecurity challenge with cybercriminals taking advantage of poor security on the part of organizations and individuals. Since Internet scams are elaborate and involve scammers gathering maximum information on victims, it can be increasingly difficult for government agencies to monitor and prevent such scams as conversations appear normal.
Email phishing remains the most popular form of internet scam with cybercriminals using texts and messages via emails to unsuspecting victims. Also, there is an increasing rate of scams perpetrated on social media and gaming platforms which has tripled in the last decade. 2019 resulted in a 50% increase in mobile banking malware attacks when compared to what was experienced in 2018. Hackers have also devised malicious applications and clone websites that steal payment details which are used to transfer money from victims’ bank accounts.
There has also been an increase in espionage with more international criminal groups interested in international markets and trade secrets. Internet scams continue to evolve in different shapes and forms and represent a major cybersecurity threat.
2. Ransomware

Ransomware limits or prevents using their computers or system through a malware program. As you may have guessed from the name, the malware requires you to pay to regain your data or system. Ransomware is one of the most common attacks today.
Unlike malware, there is an encryption key that stays on the criminal’s server. This encryption is a weapon to hold all data hostage.
Attack on company data

Ransomware has quickly shot into the top echelons of cybersecurity risks and threats in the past five years. Cybercriminals have increasingly used ransomware to target different forms of organizations with the advent of cryptocurrencies, making it easier. Sensitive organizations such as healthcare, law, and accounting firms have been targeted by hackers who encrypt health systems with ransomware and demand payments in cryptocurrencies.
Since most crypto payments cannot be easily traced, the hackers are then able to cart away with ransoms without the prying eyes of law enforcement agencies. These daring attacks have increased due to the adoption of privacy laws such as the European General Data Protection Regulation (GDPR). These laws have imposed harsh penalties on companies that fail to protect consumer data and companies within these jurisdictions.
Companies now face increasing pressures to pay hackers in the advent of ransomware or face the harsh penalties from these bodies and also tainted reputations. A cybersecurity firm, Kaspersky, has estimated that there will be more targeted ransomware with several antivirus providers focusing more on improving their anti-ransomware detection systems.
Via social media

Also, cybercriminals have leveraged social networks to get information about organizations and key members of the firms for access to sensitive data. Due to the devastating effects of ransomware, government agencies like the FBI have softened their stance towards ransom payments as the effect of releasing sensitive information could have more damage to a top firm than the payment required. This shows how destructive ransomware has been in the past few years.
Besides, organized cybercrime will actively use the capabilities of social networks to extort commercial information and conduct disinformation campaigns to damage the reputation of famous brands.
Windows 7 vulnerability

Cybercriminals have also taken advantage of the vulnerability of Windows 7 since Microsoft suspended support for the Operating system. There are fears that these could lead to security issues within developing regions that have a large number of users on the operating system. Industrial and commercial espionage is actively engaged not only by hackers but also by unscrupulous employees on the order of competitors or for personal gain.

3. Identity theft

One of the most attractive areas for cybercriminals is the financial sector. Using malware, hackers will try to infiltrate banking networks to compromise payment card data and subsequently withdraw large sums of money. Automated Process Control Systems (APCSs) look rather vulnerable to cybercriminals. Cellular operators and e-commerce companies are also at risk. In 2019, there is a high probability of noticeable leaks of biometric data, in particular, from government agencies and the health sector.
In addition, scammers also use complex methods to steal funds by directing a large section of online users to malicious exchanges and e-commerce stores. Furthermore, some cybercriminals clone financial services (where users fill in their details) and steal victims’ information. Some of these sites also have elaborate fiat to crypto gateways whereby users’ funds are withdrawn and converted to cryptocurrencies. There have been reports of such thefts across Europe and South America.
Identity theft has also become a rampant cybersecurity threat during this period of lockdown as more people are at home and browsing the Internet unprotected. There have been cases whereby cybercriminals utilize spyware to get users’ data or steal browsing history.
4. Attacks on the Internet of Things (IoT) and smartphones

There have been increasing cases of attacks by cybercriminals on the Internet of Things (IoT) networks. With the current roll-out of 5G by several countries, there are fears among security outfits regarding the safety of devices interconnected with IoT technology. Connected devices could be combined into large networks to create botnets to facilitate DDoS attacks. Furthermore, as smart city technology develops, the number of connected cars, home IoT devices, and insecure industrial sensors grows.
Some risks will increase, such as cyber-criminals increasingly spying on users through smart devices, trying to paralyze various smart city operations, and interrupting production systems. Smartphones have essentially turned into a wallet with more than 50% of the population in developed countries using their mobile devices for mobile banking. This is the reason why there has been an increase in malware for phones.
Several cybercriminal groups have focused on making Trojans for mobile phones, and the number of incidents has tripled in recent years. Android OS is the most targeted device due to its prevalence across the world. As of 2020, over 80% of smartphones operate on Android OS, and most mobile viruses are written for it specifically. It is believed that cyber-criminals infect as many as 5 million devices yearly and use this malware as a form of spyware to steal financial details.
5. Spam and phishing messages

These malicious emails appear to come from legitimate sources; however, cybercriminals send them to trick users into clicking on malicious links. This link will install malware to get sensitive information like logins, passwords, and credit card information.
Phishing
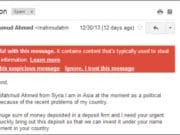
Spear-phishing is another popular method of phishing. A human hacker creates a fake social media account and tries to build commonalities among tended targets. This can include things like the same college, professional associations, or even passion for the same charities.
Phishing sites have also increased in popularity with several reports of internet users losing money and information to such sites. Now, some of them do not work; this may be due to the short life cycle of phishing sites; or may the resources be still in a “sleeping” state. These phishing sites can be used to collect user data, sell non-existent drugs, tests, or any other speculation on the topic.
Spam

Spam messages are one of the biggest threats to cybersecurity with different campaigns facilitated by cybercriminals across the world. For example, one of the most relevant spam campaigns imitates mailings from the World Health Organization. Attackers exploit user trust in this organization.
Some of these letters, which allegedly come from WHO, suggest that you click on the link to familiarize yourself with the security measures that must be taken to avoid infection. A person is redirected to a phishing site, and there, he is asked to share personal information that falls into the hands of attackers. The danger of this scheme is that it looks more realistic than others. For example, a campaign allegedly from the IMF, in which it is proposed to send donations to those who, due to the circumstances, need money.
New scam messages may also appear in which the theme of the current global pandemic, coronavirus, is exploited in one way or the other. For example, since the beginning of the year, there are more than 2500 suspicious sites in the name of which the words “covid19” and/or “coronavirus” appear. In reality, there can be many more. Another popular spam scam fraudster uses to offer victims the opportunity to take a small survey and get a large sum for the answers. After completing the survey, you must pay a small commission to facilitate the transfer of the funds. The commission could be as small as $50; and after paying such fees, the cybercriminal closes all forms of contact with you.
Recommended for you: 15+ Tips to Ensure a Secure Browsing Experience.
6. Malware

Malware can be either malicious software or malicious code. It is a program that infiltrates a system and compromises the integrity, confidentiality, and availability of data. It is done secretly and affects your operating systems, applications, and data.
Spyware is a type of malware that violates privacy policies. It can invade many systems to conduct financial fraud and also track your personal activities.

7. Denial of Service (DoS)

These cyberattacks flood a network or computer, and it prevents response to requests. While the network or computer cannot respond, the cybercriminals use this time to launch other attacks while the network or computer is down.
8. Password attacks

Cybercriminals can get a lot of vital information with the right password. Social engineering uses a strategy that relies on human interaction that helps people break security practices.
9. Man in the middle attack

This attack happens when cybercriminals get in the middle of a two-party communication. The attacker will interpret the communication and use this information to steal sensitive data. They then return different responses to the user.
10. Corporate account takeover (CATO)

This is a type of theft where a cybercriminal impersonates a business and sends unauthorized transactions. The unauthorized transactions go to the cybercriminals’ accounts.
Cybersecurity tips to stay protected online

If you think you aren’t at risk of cybercrime because your company isn’t large, think again. Believe it or not, 64% of all companies worldwide have suffered from some form of cybercrime. That means you can’t cut corners when protecting your business from online attacks.
The COVID-19 pandemic has made remote working the norm for most business organizations. However, this has intensified cybercrime and fraud as hackers discover new and sophisticated ways to access private information every day. A data breach could result in loss of revenue, increased PR, insurance, and legal costs, compromised intellectual property, and damage to your company’s reputation, so you need to find ways to prevent cyberattacks.
If you’re still trying to set up your company network to make preventing cyberattacks easy, this post will help. In this article, we highlight many useful cybersecurity tips that will help you to protect your organization by protecting your data.
1. Understand it can happen to anyone

One of the top points that make you vulnerable is the mentality that a hack wouldn’t happen to you. The truth is anyone can fall victim to a hack at any time. You don’t need to be a big corporation or a celebrity to be a target.
Change your mentality around cybersecurity and hacks. Think of how often you’re deleting junk mail. Chances are at least one of those emails contains links that could compromise your device and steal precious data (like your financial information).
2. Look for reg flags and avoid phishing scams

Although phishing email scams and virus-filled website advertisements are getting more and more sophisticated, there are warning signs to prevent you from getting caught in a virus.
Hackers and other cybercriminals use different social engineering ploys to access personal information, including employee social security numbers, login passwords and ID, and credit card and banking information. Avoid falling victim to phishing scams by not clicking or opening suspicious emails.
Before clicking on a link in an email, downloading an application, or going to a sketchy website, take a closer look first. Many phishing scams will tell a dramatic story that doesn’t always make sense. If you hover over the website first, you can often find the URL link at the bottom of your browser to confirm that’s where you’re going.
Taking that extra second to look could save your device from downloading a crippling virus.
You may like: Privacy, Security & Health Risks of Social Media & How to Prevent Those.
3. Keep your device software updated

Updates are an essential part of remaining safe and protected on the internet with whatever device you’re using. Each time you update your device, it often has new patches to fill in any holes within the device’s security features.
Constant updates can get frustrating, especially if they happen weekly. However, consider the alternative – ignoring the updates and your virus falling vulnerable to the newest virus on the market. Luckily, many devices allow you to set up automatic updates at a particular time of day or night.
The increase in security threats, including malware and other vulnerabilities, has necessitated software companies to provide software updates. The new updates are geared towards adding features to existing software, fixing known bugs, and enhancing security. Consider upgrading to the latest versions of the company’s software to protect the organization’s data from new and existing security vulnerabilities. To identify and install the latest software updates for your company’s devices, consider:
- Using various web browsers such as Chrome and Firefox to receive frequent and automatic software updates.
- Turning on automatic updates for your entity’s operating systems.
- Updating browser plugins, including Java and Flash.

4. Set up a firewall

Without a way to see what happens on your business network, it’s hard to notice and prevent hackers. You need complete visibility into what goes on in your company, and a firewall will help you do that.
Your firewall sits in front of all internet traffic in your office. It will stop hacking attempts and prevent employees from going to websites you don’t trust.
5. Use a secure Wi-Fi connection or download a VPN

The company’s devices are as secure as the networks you often use to transfer data. Even the Wi-Fi networks you and your employees use could make your business vulnerable to hacking. Ensure that you use a secure WIFI network with strong encryption to protect your organization from hackers.
You should also avoid using public Wi-Fi. Hackers and other tech-savvy users can listen to your network traffic when using public Wi-Fi, making your company’s data unsafe. If you have to access company data when traveling or out in public and have to use public Wi-Fi, ensure that you use a virtual private network (VPN) like NordVPN. Using VPN encrypts the traffic between the virtual private network servers and your devices, making it difficult for hackers to access confidential company data. Consider creating a hotspot connection with your mobile phone if you do not have VPN.
For those who connect to public networks frequently, connecting through a VPN (a virtual private network), is an excellent step to take towards cybersecurity.
A VPN creates a virtual tunnel around the connection from your device to the network. That tunnel acts as a protection against anyone or anything looking to gain access to your data as it passes from the device to the network. Without this tunnel, virtually anyone with basic hacking skills could see everything you’re doing, and even gain access to your personal data.
Now, using a VPN isn’t perfect. It’s not 100 percent effective in protecting your connection. However, it’s better than nothing, plus there are other benefits to using a VPN.
6. Do not leave devices unattended and keep your devices locked

A cyber-attack can be both technical and physical, so you should protect your business against all forms of threats. To protect your organizations from physical, cyber-attacks, you should:
- Use a secure lock on all unattended devices to protect them from being stolen or moved.
- Lock the screen if you are not using a device.
- Encrypt USB devices and portable hard drives.
Sometimes, a hack doesn’t need to be someone on a laptop across the world sneaking into your computer through software and skills. Have you ever left your laptop or smartphone sitting unattended on a table in public? As soon as you walk away with your screen open, your device is vulnerable to anyone around it.
As much as we want to rely on the goodness of individuals, it’s not always the case. Phones go missing. Laptops get swiped off tables. Anything can get stolen if it’s readily available.
Keep your devices locked at all times when they’re not in use. The newest versions of phones and laptops have face and thumbprint recognition, making it much simpler for you to lock it and gain access right when you come back. It’s not worth the risk just because adding a password isn’t the most convenient step to do.
7. Install anti-malware or anti-virus protection

As the popularity of computers and the internet increased, soon, malicious applications and data started to grow. Soon, developers saw an opportunity to offer users a service to protect them from the growing concern of computer viruses.
The first computer virus came to light in 1971 and was known as Creeper. As harmless as it was, it paved the way for newer and more sophisticated versions of the virus to grow, creating the issue we have today. Now, we have multiple versions of a computer virus wreaking havoc on computers around the world.
Antivirus software is there to protect every device from viruses trying to attack it. Not every software is built the same, though. Some prevent you from entering a website while others allow you to enter a safe mode. Other software gives you a daily report of what’s happening behind the scenes when you access the internet.
As long as you use the web to perform business transactions, your data is vulnerable to malware attacks. While it is impossible to leverage complete protection from malware, you can reduce malicious attacks by installing antivirus (AV) or antimalware protection software. Antivirus software blocks nasty viruses and malware from accessing your computer devices and compromising the organization’s data. With that being said, ensure that you purchase the antivirus device from a trusted vendor to guarantee quality. Read online reviews and testimonials or seek recommendations and referrals for leads to a reliable antivirus vendor.
Is it foolproof?
As good as a firewall prevents cybercrime, it isn’t foolproof, and it won’t block every website, and your employees will still get emails. The question is, will someone download something they shouldn’t on their computer?
Anti-malware will help stop threats if that happens. It scans your computers for new files, removes anything suspicious, and places those files in quarantine until you can examine them and remove threats.

8. Backup crucial data

An excellent security protocol isn’t worth much if an accident causes you to lose your data. While the chances of that happening are small, it can still occur. Without a reliable way to restore your lost information, your company will lose valuable time.
Backing up your data isn’t just a useful cybersecurity tip, but it’s also a good habit to get into in general. Maybe your device never gets hacked, and your data remains safe. However, what if your computer crashed and you lost everything saved on it? That can happen to basically anyone.
For cybersecurity, though, backing up your data is the best way to ensure you can gain access to your information still. Some viruses can cripple your entire system, causing you to lose everything you had on your computer. With other viruses, the only way to get rid of them is to wipe your device and reinstall the operating system completely. When you do this, you ultimately lose everything.
You could lose crucial business data in case of a security breach, which may result in reduced credibility among your clients. Consider backing up important company information to make it easier to retrieve if your server crashes, the hard disk gets damaged, or during a security breach.
Invest in a backup solution to safeguard your information. There are various ways you could backup vital company information, including:
a) Local backup

Local backup or on-premises backup involves copying crucial company data in storage devices such as optical disks and hard drives kept in-house. Data backup and recovery are generally quicker with on-premises backup since the storage disks can easily be retrieved. You also do not have to wait for a virtual system to make a connection. However, hard drives and optical disks can be stolen, damaged, or lost, so you can quickly lose backed-up data. You could also lose crucial information in case of a disaster that results in structural damage as these backups are stored on-site.
b) Cloud backup

Cloud backup, also known as online-based backup, uses off-site technologies to host backups. Since you do not require hardware to backup data in the cloud, online-based backups are pretty affordable. Backing up data in the cloud is also quicker as you can develop a solution that continually backs up information. However, this requires a faster bandwidth connection, so you have to invest in a more sophisticated network infrastructure, which can be expensive.
Recommended for you: Documents and Protocols Your Business Needs for Cybersecurity.
9. Use strong passwords

Passwords are your first defense to keep your accounts and devices safe. When you create an account for something, your password is what prevents anyone from logging on and accessing your information. Without it, you’re basically inviting anyone and everyone to use your account. Creating a solid and complex password is the first step to protecting your organization’s data.
There are many tips for using strong passwords. You want to use a long enough password that it’s hard to guess without you forgetting it. To create a unique and secure password, ensure it has at least 10 characters and consists of numbers, upper case, lower case, and special characters such as #, @, $, and &. Use something that you’ll easily remember, but something that any individual that knows you still wouldn’t guess (for example, don’t use your birthday or the year you were married).
Other tips include using different passwords for different accounts and changing them frequently. Alternatively, you could consider using passwordless authentication. Going passwordless saves you the hassle of remembering a complex password, especially when you have multiple passwords for different platforms. Facial recognition or fingerprints are excellent examples of passwordless authentication.
10. Manage your passwords

You should vary your passwords, especially when you have multiple accounts. This ensures that even if specific credentials get stolen, they will not work on other accounts. However, it may be challenging to recall multiple long passwords for different sites, so you should consider using a password manager such as Dashlane, 1Password, or LastPass, to mention a few. You just have to recall one long, complex password to access other passcodes with a password manager. Remember to keep updating and changing this passcode to make it more secure. You should also avoid sharing this password with your employees.

11. Look into two-factor or multi-factor authentication

With today’s advancements, you can use more than a password to keep your accounts secured. No matter how secure or complex your passwords are, hackers have ways of figuring them out, making your organizations and customer data vulnerable to theft. So, you should consider implementing two-factor authentication. Two-factor (or multi-factor) authentication is an extra level of protection for your device and your data.
Multi-factor authentication is what it sounds like – it’s additional security mechanisms you use for logging into something. It could be biometrics (thumbprint), a numerical code, or even a phone call to a selected number. Using this service increases the security of anything you use it on, especially if it sends a code to your personal cellphone.
Two-factor authentication (2FA) adds an extra layer of protection for your organization’s data. It requires you to input a randomly generated code sent to your email or phone, along with your username and password, to access your accounts. This ensures only authorized personnel access crucial company data. Since the verification code is generated one time, it may be challenging for hackers to figure it out.
12. Use mobile devices securely

Today, most organizations rely on mobile phones to perform most business transactions, exposing the company to more cyber threats. According to research by McAfee Labs, the mobile phone is now vulnerable to more than 1.5 million incidents of mobile malware, so you should consider using these devices securely.
The following are quick tricks to ascertain mobile device safety:
- Lock your phone with a complex password or pin and avoid leaving it unsecured, especially when in public.
- Download and install applications from trusted and reliable sources such as Google Play and Apple AppStore.
- Avoid sharing sensitive or PII information via emails or text messages.
- Prevent mobile phone theft or loss by using the Android Device Manager or Find My iPhone tools.
- Keep the mobile phone’s operating system up to date.
- Avoid clicking attachments or links from unsolicited texts and emails.
13. Encrypt your company’s data

End-to-end encryption provides an effective way to protect the confidentiality of your business data when in transit or at rest. It entails scrambling business data into a secret code before sending it to a designated recipient. To decode the information, the recipient must have a decryption key. This ensures that only authorized eyes have access to transmitted data, so you do not have to worry about private company files getting exposed.
14. Remove adware from the company’s devices

Adware gathers information about your company’s machines to provide targeted ads. However, this information could fall into the wrong hands, resulting in a security breach. To protect your organization, consider investing in anti-adware to eliminate all kinds of adware.

15. Stay informed and keep your security knowledge current

Since security is a vast field and cybercriminals are constantly fishing for new ways to access private information, you need to keep your security knowledge up to date. Avoid focusing solely on handling current business emergencies. Instead, enroll in an online course to get current on cybersecurity topics and issues such as cyber threats, risk assessment, physical security, and threat detection, to mention a few. This helps you handle and protect your organization from cyber threats no matter how sophisticated hackers’ tricks get.
Stay informed about the cybersecurity world, and the latest threats is another level of protection. If you’re aware of what is potentially out there threatening your data, you can take steps to prevent anything from happening, rather than reacting to a situation.
Sign up for newsletters that talk about cybersecurity and any new viruses or phishing scams popping up. Read about the latest hack of a large corporation to see if any of your personal information was affected. The more you can stay in the know, the better you can protect yourself.
16. Educate employees on cybersecurity

One of the greatest risks to an organization’s cybersecurity is employee negligence. Employees often open suspicious links that infect the company’s computer system with malware, expose sensitive organization data through their mobile phones, and fall victim to phishing scams.
Believe it or not, your employees are one of your most significant concerns when you try to secure a business network. Even if you have great security products and procedures, hackers can still compromise your business if a team member does something they shouldn’t.
That makes employee training a must when running a small business. To protect your organization, you should consider raising employee awareness through training to sensitize the importance of security protocols and data protection. Create a training program for every employee to go through and require completion of that program before allowing someone access to company data.
17. Audit cloud software

You don’t have zero risk when relying on cloud tools like npit.co.uk for your software. The data you store in the cloud is still sensitive. You’ll put it at risk if you use a cloud provider that doesn’t take security seriously.
Before using a cloud provider’s service, ask them how they handle internet security. If they don’t give you confidence with their answer, look for another software provider.
You may also like: VPN vs Antidetect Browsers – Which One to Choose?
There are more cybersecurity tips out there

The number of cybersecurity threats increases every year, so you can’t rest easy when you need to protect sensitive data. You need to be on the lookout for more cybersecurity tips to ensure you’re well protected in the future. Keep improving your internet security as time goes on to ensure hackers can’t break into your network.
If you want to learn more about tech and how it can help your company, head back to the blog. You’ll learn how to use tech tools to make your business more productive.
Conclusion

Over the recent years, data breaches and cyber-attacks have gained more proliferation. This makes it more critical for you to be more aware and prepared of the new and existing threats to your company’s cybersecurity. Familiarize yourself with the above cybersecurity tips to keep doors locked on your organization’s data.
This article discussed the major cybersecurity threats faced by internet users around the globe today. The discussion of these major cybersecurity threats serves as a reminder that internet users need to be more proactive with internet security and take protective measures when browsing online. Such measures can include the use of strong passwords, the use of VPNs, 2-factor authentication, etc.
Cybersecurity doesn’t have to be challenging or filled with complicated steps. Sometimes, the simplest things like your password or downloading antivirus software are enough to keep you protected. However, taking more steps is never a bad thing. Think about what all on your smartphone or your laptop is. Now, imagine if a stranger got a hold of your device. Would they have free access to all the information on it, or would you frustrate them enough to give up because you have additional security steps to get through? A good reminder is if your security efforts annoy you, chances are they would annoy someone who shouldn’t be using your device.
We have written this article in association with Nicole Luke. Nicole is a creative content writer at Superinternetdeals.com. She is living in New Jersey and has been working in the field of content writing for many years.





